Čo je CAPTCHA? Komplexný sprievodca

V neustále sa vyvíjajúcom prostredí internetovej bezpečnosti je jednou z pretrvávajúcich výziev prevencia automatizovaného zneužívania. CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart – Celkom automatizovaný verejný Turingov test na rozlíšenie počítačov a ľudí) bola navrhnutá na boj proti tomuto problému, pričom rozlišuje medzi ľudskými používateľmi a škodlivými robotmi prostredníctvom prezentovania úloh, ktoré sú pre ľudí jednoduché, ale pre stroje ťažké. CAPTCHA sa bežne používa na ochranu formulárov, prihlasovacích stránok, registračných procesov a všade tam, kde je ľudské overenie kritické na zabezpečenie toho, aby automatizované skripty nemohli pristupovať k webovým službám alebo s nimi manipulovať.
Význam CAPTCHA v oblasti webovej bezpečnosti spočíva v jej schopnosti predchádzať rôznym typom kybernetických útokov. Či už ide o zabránenie robotom v spamovaní kontaktných formulárov, marenie pokusov o prihlásenie hrubou silou alebo ochranu pred útokmi pomocou ukradnutých prihlasovacích údajov, CAPTCHA sa stala základným bezpečnostným opatrením vo webovom vývoji.
CAPTCHA sa však od svojho vzniku značne vyvinula. Skoré verzie boli rudimentárne, s hádankami s deformovaným textom. V súčasnosti existujú sofistikovanejšie formy, ako sú napríklad hádanky založené na obrázkoch, neviditeľné CAPTCHA a alternatívy poháňané umelou inteligenciou. Keďže útočníci našli nové spôsoby, ako obísť tieto systémy, poskytovatelia CAPTCHA neustále inovovali, aby si udržali náskok. V tomto článku sa ponoríme do rôznych typov CAPTCHA, preskúmame popredných poskytovateľov CAPTCHA, prediskutujeme bezpečnostné dôsledky a poskytneme osvedčené postupy pre integráciu CAPTCHA do moderných webových aplikácií.
Typy CAPTCHA
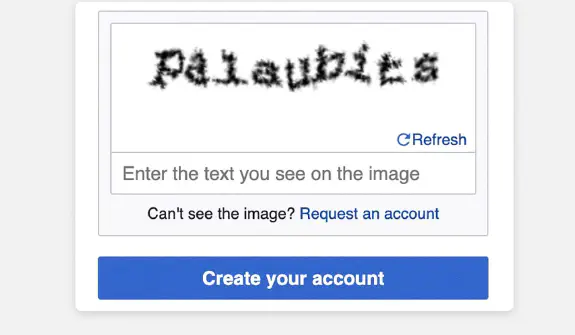
Textová CAPTCHA
Textová CAPTCHA bola pôvodnou formou, ktorá používateľom bežne predkladala deformovaný alebo zakrytý text, ktorý museli prepísať. Tieto úlohy sú často manipulované rôznymi technikami zatemňovania, ako je pridávanie šumu, otáčanie textu a deformovanie znakov, aby sa robotom sťažila interpretácia.
Výhody:
- Jednoduchá implementácia
- Nízka hmotnosť, minimálna výkonnostná réžia
Nevýhody:
- Slabá používateľská skúsenosť z dôvodu ťažkostí s čítaním textu
- Možnosť obísť pomocou nástrojov na optické rozpoznávanie znakov (OCR), najmä s pokrokmi v modeloch strojového učenia
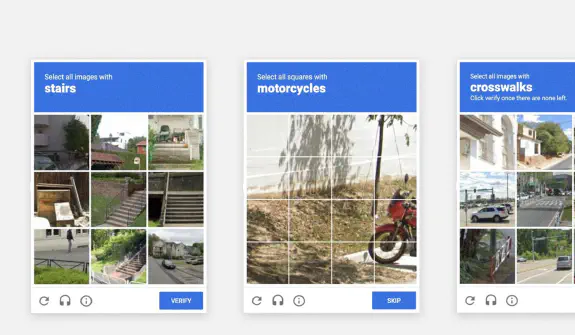
Obrázková CAPTCHA
Jednou z modernejších foriem CAPTCHA je obrázková CAPTCHA, ktorá vyzýva používateľov, aby identifikovali obrázky, ktoré spĺňajú určité kritérium, ako napríklad vyberte všetky semafory
alebo kliknite na všetky obrázky obsahujúce auto.
Tento typ CAPTCHA je populárny pre svoj intuitívny model interakcie a pre roboty je ťažšie ho prelomiť.
Výhody:
- Všeobecne jednoduchšia na vyriešenie pre používateľov v porovnaní s textovou CAPTCHA
- Pre roboty ťažšie prelomiť kvôli kontextovej povahe rozpoznávania obrázkov
Nevýhody:
- Náročnejšia na šírku pásma a výkon z dôvodu načítavania viacerých obrázkov
- Problémy s prístupnosťou pre používateľov so zrakovým postihnutím
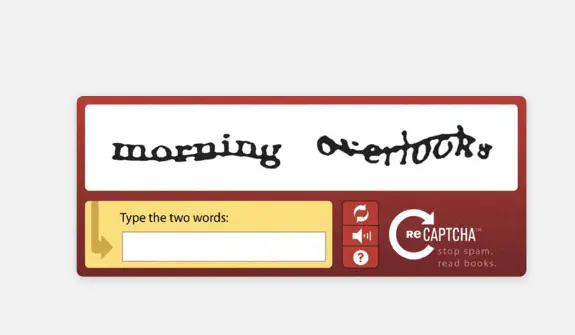
Audio CAPTCHA
Na zlepšenie prístupnosti pre používateľov so zrakovým postihnutím bola zavedená zvuková CAPTCHA. Poskytuje zvukovú nahrávku, ktorú si používatelia musia vypočuť a prepísať.
Výhody:
- Ponúka spôsob, ako môžu používatelia so zrakovým postihnutím prejsť CAPTCHA
Nevýhody:
- Často ťažko zrozumiteľná kvôli hluku v pozadí
- Nevhodná pre používateľov so sluchovým postihnutím
- Zraniteľná voči softvéru na rozpoznávanie reči
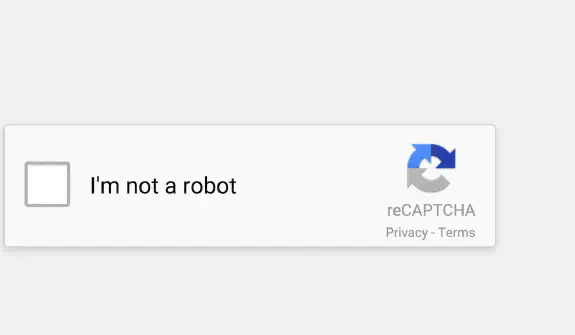
NoCAPTCHA reCAPTCHA (Google reCAPTCHA v2 a v3)
Google reCAPTCHA je už dlho popredným poskytovateľom CAPTCHA. Vydaním NoCAPTCHA reCAPTCHA v2 sa spoločnosť Google posunula smerom k používateľsky prívetivejším CAPTCHA, kde používatelia často len zaškrtnú políčko s textom Nie som robot
. V zákulisí Google vyhodnocuje správanie používateľov, ako sú pohyby myši a časovanie kliknutí, aby posúdil, či ide o človeka alebo robota.
reCAPTCHA v3 ide o krok ďalej analýzou interakcií používateľov na celej webovej lokalite a priradením skóre rizika
bez toho, aby si vyžadovala akúkoľvek priamu interakciu používateľa, čím sa CAPTCHA stáva neviditeľnou pre väčšinu legitímnych používateľov.
Výhody:
- Vynikajúca používateľská skúsenosť vďaka zníženej interakcii
- Pokročilé bezpečnostné opatrenia analyzujúce správanie používateľov
Nevýhody:
- Obavy o súkromie, pretože sa sleduje správanie a aktivita používateľov
- Stále môže blokovať legitímnych používateľov, ak je ich správanie nezvyčajné
Neviditeľná CAPTCHA a moderné riešenia
Moderné služby CAPTCHA, ako napríklad hCaptcha a FunCaptcha, sa zameriavajú na neviditeľné alebo takmer neviditeľné metódy, ktoré vyžadujú malú alebo žiadnu interakciu používateľa. Tieto systémy sa vo veľkej miere spoliehajú na behaviorálnu analýzu, pokročilé algoritmy a strojové učenie na detekciu, či je návštevník človek alebo robot.
- hCaptcha: Podobná ako reCAPTCHA, ale s väčším dôrazom na postupy ochrany osobných údajov. Je navrhnutá tak, aby chránila používateľov bez rozsiahleho sledovania, ako to robí Google.
- FunCaptcha: Používa hravé hádanky, ktoré si vyžadujú minimálne úsilie používateľa, ale stále predstavujú výzvy pre roboty. Je uznávaná pre poskytovanie pútavejšej používateľskej skúsenosti.
Výhody:
- Neviditeľná pre používateľov, čím sa zlepšuje celkový dojem
- Pokročilé bezpečnostné modely využívajúce umelú inteligenciu a strojové učenie
- Súlad s normami ochrany osobných údajov (napr. GDPR)
Nevýhody:
- Náročná na zdroje a môže ovplyvniť výkon
- V niektorých prípadoch zložité integračné procesy
Prehľad služieb CAPTCHA
Niekoľko populárnych poskytovateľov CAPTCHA, ako napríklad Google reCAPTCHA (otvorí sa v novom okne), CloudFlare TurnStile (otvorí sa v novom okne), hCaptcha (otvorí sa v novom okne) a FunCaptcha (otvorí sa v novom okne) dominujú tomuto prostrediu. Každá služba má svoje silné a slabé stránky, pokiaľ ide o bezpečnosť, používateľskú skúsenosť a jednoduchosť integrácie.
Google reCAPTCHA
- Sila zabezpečenia: Google reCAPTCHA v3 je vysoko efektívna, využíva rozsiahly súbor údajov Google na detekciu a prevenciu robotov. Zavedenie systému hodnotenia rizika vo verzii v3 ju robí ešte sofistikovanejšou.
- Jednoduchosť integrácie: Bezproblémovo sa integruje s väčšinou rámcov a knižníc.
- Používateľská skúsenosť: Interakcia používateľa je minimálna s v2 (zaškrtávacie políčko) a neexistujúca s v3 (neviditeľná).
- Výkon: Minimálny dopad na výkon; existujú však obavy o súkromie kvôli sledovaniu správania používateľov spoločnosťou Google na webových stránkach.
- Prístupnosť: Zvukové alternatívy existujú, ale môžu byť ťažko zrozumiteľné.
hCaptcha
- Sila zabezpečenia: Porovnateľná s Google reCAPTCHA, ale s väčším zameraním na súkromie. Je obzvlášť účinná pre spoločnosti, ktoré sa obávajú dodržiavania zákonov o ochrane údajov.
- Jednoduchosť integrácie: Jednoduchá pre väčšinu platforiem, podobne ako reCAPTCHA.
- Používateľská skúsenosť: Možnosti neviditeľnej CAPTCHA zlepšujú používateľskú skúsenosť.
- Výkon: Mierny dopad na výkon, ale vo všeobecnosti nenáročná v porovnaní s obrázkovými CAPTCHA.
- Prístupnosť: Zameriava sa na dodržiavanie noriem WCAG (Web Content Accessibility Guidelines – Pokyny pre prístupnosť webového obsahu).
FunCaptcha
- Sila zabezpečenia: Silná v prevencii robotov, najmä s hravými hádankami, ktoré sa prispôsobujú rôznym úrovniam hrozieb.
- Jednoduchosť integrácie: Relatívne jednoduchá integrácia do hlavných webových rámcov.
- Používateľská skúsenosť: Pútavejšia, s rýchlymi a intuitívnymi hádankami pre používateľa.
- Výkon: Nízky dopad na rýchlosť načítavania vďaka nenáročnej povahe hádaniek.
- Prístupnosť: Niektoré obavy týkajúce sa prístupnosti, pretože nie všetky hádanky sú navrhnuté pre používateľov so zdravotným postihnutím.
Bezpečnostné dôsledky
CAPTCHA zohráva kľúčovú úlohu v oblasti webovej bezpečnosti a poskytuje vrstvu ochrany pred rôznymi automatizovanými útokmi. Rozsah ich účinnosti sa však líši v závislosti od ich implementácie, typu CAPTCHA a vyvíjajúcej sa sofistikovanosti automatizovaných skriptov a robotov. Nižšie analyzujeme, ako sa CAPTCHA bráni proti niekoľkým bežným bezpečnostným hrozbám.
Roboty a automatizované útoky
Automatizované skripty alebo roboty sa môžu používať na škodlivé účely, ako je napríklad útok pomocou ukradnutých prihlasovacích údajov, extrahovanie citlivých údajov alebo vykonávanie útokov DDoS (Distributed Denial of Service – Distribuované odmietnutie služby). Rozlišovaním medzi ľudskými používateľmi a robotmi CAPTCHA zabraňuje tomu, aby takéto útoky preťažili webovú lokalitu alebo službu. Zložitosť CAPTCHA, ako sú deformované textové alebo obrázkové varianty, sťažuje jednoduchým robotom prejsť.
- Textové CAPTCHA: Tie spochybňujú schopnosť robota rozpoznávať znaky, čím bránia základným automatizovaným skriptom v dokončení formulárov.
- reCAPTCHA v3: Namiesto predkladania úloh beží ticho na pozadí, aby posúdila správanie, pričom detekuje robotov na základe vzorcov aktivity.
Útoky hrubou silou na prihlásenie
Útoky hrubou silou zahŕňajú systematické hádanie používateľských mien a hesiel s cieľom získať neoprávnený prístup. Vyžadovaním dokončenia CAPTCHA po určitom počte neúspešných pokusov o prihlásenie môžu webové stránky zastaviť útoky hrubou silou. To pridáva značné oneskorenie ku každému neúspešnému prihláseniu, čím sa hrubá sila stáva pre hackerov nepraktickou.
- Implementácia: Bežné stratégie zahŕňajú zobrazenie CAPTCHA po 3 – 5 neúspešných pokusoch o prihlásenie alebo vtedy, keď sa správanie pri prihlásení zdá nezvyčajné.
- Zmiernenie: reCAPTCHA v3 dokáže automaticky detekovať podozrivé pokusy o prihlásenie bez predkladania úloh, čo z nej robí silnú voľbu pre ochranu prihlásenia.
Spam a podvodné registrácie
Roboty môžu registrovať falošné kontá, odosielať spamový obsah alebo vykonávať podvodné akcie, ktoré ohrozujú integritu webovej lokality alebo jej komunity. CAPTCHA bráni robotom v dokončení formulárov pre akcie, ako je vytváranie kont, uverejňovanie komentárov alebo odosielanie správ.
- hCaptcha: Obzvlášť populárna na prevenciu falošných registrácií, hCaptcha ponúka lepšie stimuly pre vlastníkov webových stránok, pretože im platí za dokončenie CAPTCHA, pričom zároveň účinne zastavuje robotov pred spamovaním registračných formulárov.
- Neviditeľné CAPTCHA: Tie fungujú bez narušenia používateľskej skúsenosti a zároveň ticho blokujú automatizované roboty pred vypĺňaním formulárov.
Obavy týkajúce sa prístupnosti a bezpečnostné kompromisy
Zatiaľ čo CAPTCHA zvyšuje bezpečnosť, niekedy môže brániť legitímnym používateľom, najmä používateľom so zdravotným postihnutím. Zvukové CAPTCHA, hoci sú navrhnuté tak, aby pomáhali používateľom so zrakovým postihnutím, nie sú vždy účinné z dôvodu zlej kvality zvuku alebo jazykových bariér. Preto je dôležité nájsť rovnováhu medzi bezpečnosťou a prístupnosťou používateľov.
- Problémy s prístupnosťou: Výber obrázkov v reCAPTCHA v2 môže byť náročný pre používateľov s kognitívnym alebo motorickým postihnutím.
- Zmiernenie: Poskytovanie alternatívnych metód overovania, ako sú biometrické systémy alebo behaviorálna analýza riadená umelou inteligenciou, zaisťuje prístupnosť pri zachovaní bezpečnosti.
Výzvy a obchádzanie
Hoci CAPTCHA poskytuje líniu obrany proti robotom, nie je neomylná. Útočníci vyvinuli niekoľko techník na obídenie systémov CAPTCHA, ktoré sa neustále vyvíjajú, aby riešili tieto zraniteľnosti.
CAPTCHA farmy
Jedným z najbežnejších spôsobov, ako obísť CAPTCHA, je použitie CAPTCHA fariem. Ide o služby, kde ľudskí pracovníci riešia CAPTCHA v reálnom čase za malý poplatok, čím útočníkom poskytujú správne odpovede.
- Dopad: CAPTCHA farmy dramaticky znižujú účinnosť tradičných CAPTCHA, pretože ľudskí riešitelia na ne dokážu odpovedať s vysokou presnosťou.
- Zmiernenie: Riešenia ako reCAPTCHA v3, ktoré monitorujú správanie používateľov namiesto vyžadovania priamej interakcie, pomáhajú znížiť závislosť od úloh CAPTCHA a obmedziť vystavenie CAPTCHA farmám.
Modely strojového učenia
Modely strojového učenia, najmä tie, ktoré sú vyškolené na rozpoznávanie vzorov v systémoch CAPTCHA, sa stali významnou výzvou. Napríklad textové CAPTCHA sú zraniteľné voči systémom optického rozpoznávania znakov (OCR), ktoré boli vyladené na riešenie deformovaného textu.
- Obrázkové CAPTCHA: Modely strojového učenia trénované na súboroch údajov o rozpoznávaní obrázkov teraz dokážu presne identifikovať objekty v úlohách CAPTCHA, čím prekonávajú obrázkové systémy.
- Zmiernenie: Poskytovatelia CAPTCHA neustále vyvíjajú svoje algoritmy, zavádzajú novšie a zložitejšie hádanky alebo sa spoliehajú na behaviorálnu analýzu, ktorá je menej náchylná na automatizované obchádzanie.
Roboty s bezhlavými prehliadačmi
Útočníci často používajú bezhlavé prehliadače (prehliadače bez používateľského rozhrania) na interakciu s webovými stránkami a zároveň sa vyhýbajú detekcii. Tieto bezhlavé prehliadače dokážu simulovať ľudské akcie, ako sú pohyby myši a kliknutia, aby obišli určité typy systémov CAPTCHA.
- Zmiernenie: Kombinácia CAPTCHA s nástrojmi behaviorálnej analýzy, ako je reCAPTCHA v3, alebo nasadenie pokročilých techník fingerprintingu (sledovanie pohybu myši, vzorcov úderov klávesov) môže pomôcť identifikovať a blokovať roboty používajúce bezhlavé prehliadače.
Obmedzenia systémov CAPTCHA
CAPTCHA nie je bez obmedzení. Môže frustrovať používateľov, ovplyvniť celkovú používateľskú skúsenosť a je náchylná na problémy s prístupnosťou. Okrem toho, ako sa systémy CAPTCHA stávajú sofistikovanejšími, stávajú sa sofistikovanejšími aj metódy na ich prekonanie.
- Dopad na UX: Zložité CAPTCHA môžu odradiť používateľov od dokončenia akcií na stránke, čo by mohlo viesť k opusteným registráciám alebo formulárom.
- Alternatívne riešenia: CAPTCHA by sa mala kombinovať s inými bezpečnostnými opatreniami, ako je obmedzenie rýchlosti, čierne listiny IP adries a fingerprinting zariadení, aby sa posilnila celková bezpečnosť.
Osvedčené postupy pre integráciu
Výber správneho riešenia CAPTCHA a jeho správna implementácia sú životne dôležité kroky pri zvyšovaní bezpečnosti aj používateľskej skúsenosti. Nižšie sú uvedené niektoré osvedčené postupy, ktoré treba dodržiavať pri integrácii riešení CAPTCHA do vašich webových aplikácií.
Ako si vybrať správnu CAPTCHA pre svoju stránku
Rôzne systémy CAPTCHA vyhovujú rôznym potrebám. Napríklad blog s nízkou návštevnosťou môže potrebovať len základnú textovú CAPTCHA, zatiaľ čo webová lokalita elektronického obchodu, ktorá sa zaoberá platbami a citlivými údajmi, môže vyžadovať pokročilejšie možnosti, ako je reCAPTCHA v3 alebo biometrické CAPTCHA.
- Zvážte svoje publikum: Pre stránky určené pre používateľov so zdravotným postihnutím uprednostnite prístupnosť. Zvukové CAPTCHA a neviditeľné riešenia môžu byť vhodnejšie.
- Analyzujte bezpečnostné potreby: Stránky náchylné na útoky, ako sú finančné služby alebo rozsiahle platformy elektronického obchodu, môžu potrebovať sofistikovanejšie riešenia CAPTCHA v kombinácii s dodatočnými bezpečnostnými opatreniami.
Integrácia v rôznych webových technológiách
Integrácia CAPTCHA sa líši v závislosti od zásobníka technológií vašej webovej lokality. Väčšina poskytovateľov CAPTCHA ponúka knižnice alebo SDK pre rýchlu integráciu do populárnych rámcov, ako sú Django, Flask, Node.js a React.
- Frontendové rámce: reCAPTCHA alebo hCaptcha sa dajú jednoducho vložiť do frontendových formulárov prostredníctvom jazyka JavaScript. Bezproblémovo fungujú s React, Angular alebo Vue.js.
- Backendová integrácia: Validácia na strane servera je kľúčová na zabezpečenie toho, aby boli výsledky CAPTCHA skutočné. Napríklad použitie validačného API Google reCAPTCHA v Node.js, Django alebo Flask zaisťuje, že token CAPTCHA je správne overený pred povolením odoslania formulára alebo prihlásenia.
Kombinácia CAPTCHA s inými bezpečnostnými opatreniami
Spoliehať sa výlučne na CAPTCHA nestačí. Tu sú doplnkové bezpečnostné techniky, ktoré môžu zvýšiť vašu obranu:
- Obmedzenie rýchlosti: Obmedzenie počtu žiadostí z jednej IP adresy v krátkom časovom období pomáha zmierniť útoky hrubou silou.
- Čierne listiny IP adries: Blokovanie IP adries známych škodlivou aktivitou môže zabrániť útokom skôr, ako dosiahnu štádium CAPTCHA.
- Fingerprinting zariadení: Sledujte informácie o zariadení používateľov (typ prehliadača, operačný systém atď.) na detekciu podozrivej aktivity.
Budúcnosť CAPTCHA
Keďže sa systémy CAPTCHA aj metódy útokov vyvíjajú, budúcnosť CAPTCHA spočíva v integrácii umelej inteligencie, biometrie a vylepšenej behaviorálnej analýzy. Tieto pokroky pravdepodobne znížia trenie pre legitímnych používateľov a zároveň čoraz viac sťažia robotom obchádzanie bezpečnostných opatrení.
CAPTCHA riadená umelou inteligenciou
Očakáva sa, že budúca generácia systémov CAPTCHA využije umelú inteligenciu na presnejšiu identifikáciu správania používateľov. Namiesto toho, aby používateľov žiadala o riešenie hádaniek, umelá inteligencia bude analyzovať vzorce, ako je pohyb myši, kadencia písania a správanie pri navigácii, aby určila, či je používateľ človek alebo robot.
- Úloha umelej inteligencie: CAPTCHA riadená umelou inteligenciou, ako napríklad Google reCAPTCHA v3, sa zameriava na úplné odstránenie úloh a tiché monitorovanie správania používateľov.
- Behaviorálna analýza: Naučením sa, ako sa správajú legitímni používatelia, môžu tieto CAPTCHA časom zlepšiť svoju presnosť, čím sa zníži pravdepodobnosť falošného označenia legitímnych používateľov.
Biometrické overovanie
Biometrické metódy overovania, ako je snímanie odtlačkov prstov, rozpoznávanie tváre a rozpoznávanie hlasu, môžu nakoniec nahradiť tradičné CAPTCHA, najmä v aplikáciách s vysokou citlivosťou, ako sú bankovníctvo alebo zdravotníctvo. Tieto metódy ponúkajú silnejšie bezpečnostné záruky a roboty ich ťažšie napodobňujú.
- Výhody: Biometria ponúka vysokú bezpečnosť bez ovplyvnenia používateľskej skúsenosti, pretože používatelia sú už zvyknutí používať biometrické systémy na mobilných zariadeniach.
- Výzvy: Implementácia biometrickej CAPTCHA v rozsiahlejšom meradle si vyžaduje sofistikovaný hardvér a softvér, čo nemusí byť realizovateľné pre všetky webové stránky.
Neviditeľné a kontextovo vedomé CAPTCHA
V budúcnosti sa CAPTCHA pravdepodobne stane kontextovo uvedomelejšou a bude využívať dátové body, ako sú história prehliadania, informácie o zariadení a vzorce interakcie, na detekciu podozrivej aktivity. Tieto neviditeľné CAPTCHA budú ticho analyzovať používateľov bez toho, aby narušili ich skúsenosť.
Hybridné riešenia: Kombinácia CAPTCHA a viacfaktorového overenia (MFA)
Keďže útoky sú čoraz sofistikovanejšie, kombinácia CAPTCHA s MFA sa stáva čoraz populárnejším trendom. Tento hybridný prístup zaisťuje, že aj keď je CAPTCHA obídená, na získanie prístupu sa stále vyžaduje dodatočná vrstva zabezpečenia (napríklad jednorazové heslo alebo biometrické overenie).
Záver: Vyvažovanie bezpečnosti, použiteľnosti a prístupnosti
CAPTCHA zostáva kľúčovým prvkom webovej bezpečnosti a ponúka ochranu pred automatizovanými robotmi, útokmi hrubou silou a spamom. Keďže sa však schopnosti útočníkov vyvíjajú, musia sa vyvíjať aj naše prístupy k implementácii CAPTCHA. Pochopenie rôznych typov služieb CAPTCHA, ich silných a slabých stránok a spôsobov ich efektívnej integrácie je nevyhnutné pre webových vývojárov a špecialistov na IT bezpečnosť.
Kľúčové poznatky
- Dôležitosť CAPTCHA: CAPTCHA poskytuje potrebnú bariéru proti automatizovaným útokom, zvyšuje bezpečnosť a zároveň chráni citlivé údaje a integritu používateľov.
- Rozmanité typy CAPTCHA: Rôzne typy CAPTCHA vyhovujú rôznym bezpečnostným potrebám a používateľským skúsenostiam. Textové, obrázkové, zvukové a moderné neviditeľné CAPTCHA slúžia na jedinečné účely a pochopenie ich silných stránok a kontextov použitia je kľúčové.
- Bezpečnostné hľadiská: Hoci sú CAPTCHA účinné proti mnohým hrozbám, nie sú úplne spoľahlivé. Vznik CAPTCHA fariem, strojového učenia a iných pokročilých techník poukazuje na potrebu neustáleho vývoja technológie CAPTCHA a integrácie s ďalšími bezpečnostnými opatreniami.
- Osvedčené postupy integrácie: Správna integrácia je životne dôležitá pre efektívnosť aj používateľskú skúsenosť. Výber správnej CAPTCHA pre vašu aplikáciu, zohľadnenie prístupnosti a použitie doplnkových bezpečnostných opatrení môže výrazne zvýšiť vašu obranu.
- Budúce trendy: Pri pohľade do budúcnosti prinášajú rozvíjajúce sa technológie, ako sú CAPTCHA riadená umelou inteligenciou a biometrické overovanie, prísľub zlepšenia bezpečnosti pri minimalizácii trenia používateľov. Posun smerom k neviditeľným a kontextovo uvedomelým CAPTCHA signalizuje posun smerom k bezproblémovejším interakciám používateľov.
Záverečné myšlienky
Pre webových vývojárov a bezpečnostných profesionálov je neustálou výzvou zvyšovanie bezpečnostných opatrení bez ohrozenia používateľskej skúsenosti. CAPTCHA zohráva neoddeliteľnú úlohu v tejto rovnováhe a jej vývoj bude aj naďalej formovať prostredie webovej bezpečnosti. Tým, že zostaneme informovaní o pokrokoch v technológii CAPTCHA a premyslene ich integrujeme, môžeme vytvoriť bezpečnejšie a používateľsky prívetivejšie online prostredia.
Zameraním sa na robustné riešenia CAPTCHA a ich kombináciou s inými bezpečnostnými postupmi môžeme lepšie chrániť naše webové lokality pred rastúcim množstvom online hrozieb a zároveň zabezpečiť pozitívnu skúsenosť pre našich používateľov. S pokrokom technológií sa musia vyvíjať aj naše stratégie v nikdy nekončiacom boji proti škodlivým robotom a automatizovaným útokom. Ak chcete zlepšiť bezpečnosť svojej webovej lokality, nechajte spoločnosť Playful Sparkle, aby vám pomohla pri nastavovaní efektívnych riešení CAPTCHA , ktoré zvyšujú ochranu bez obetovania používateľskej skúsenosti.
Zdroje
Spoločne posuňme váš úspech na vyššiu úroveň!
Vyžiadajte si bezplatnú cenovú ponukuSúvisiace články

Návod: Ako zvýšiť bezpečnosť WordPress webu v roku 2024
Dôležitosť bezpečnosti webovej stránky pre WordPress stránky WordPress poháňa viac ako 40 % všetkých webových stránok na internete, čo z neho robí prvoradý cieľ pre hackerov. Prečítajte si viaco Návod: Ako zvýšiť bezpečnosť WordPress webu v roku 2024

Ovládnutie Cloudflare: Komplexný sprievodca kľúčovými funkciami a vlastnosťami
V oblasti moderného webového vývoja a internetovej bezpečnosti sa CloudFlare etabloval ako jeden z najdôležitejších nástrojov pre webových vývojárov aj expertov na kybernetickú bezpečnosť. Prečítajte si viaco Ovládnutie Cloudflare: Komplexný sprievodca kľúčovými funkciami a vlastnosťami

Výhody používania profesionálnej e-mailovej adresy pre podnikanie
Vaša e-mailová adresa neslúži len ako komunikačný nástroj, ale je aj kľúčovou súčasťou identity vašej spoločnosti. Aký dojem zanechávate na klientov, zákazníkov alebo partnerov, keď od Vás obdržia e-mail? Prečítajte si viaco Výhody používania profesionálnej e-mailovej adresy pre podnikanie

